Let’s start with a standard scenario where I have a development environment project, for example, development-project. We have tested logic for a new application and the we were using best practices having created a service account and roles. We have one role which maintains the key privileges that our service account uses via our application to control some aspects of GCP such as virtual machine creation.
We now need to migrate incrementally or otherwise a new feature that requires the updated permissions. The role does not yet exists in our production GCP project, production-project. So how do we copy the role, vm-svc-usr-role, from development-project, to our production-project? Let’s take a look
We will use the native cli for gcloud, using the segment iam, and the function, roles copy.
This can be detailed in the documentation, of course, https://cloud.google.com/sdk/gcloud/reference/iam/roles/copy
first, let’s open a terminal window (or command line terminal) and run the command for gcloud to show us what our current configuration settings are on our local development machine or laptop. In the terminal window, type in, gcloud config list
This will list out any prominent information about the current default project, etc.
look for the project attribute and determine if this is the project name where the gcp role currently exists. If not, then you can change the project default by running, gcloud config set project = development-project for example
Navigate to your google cloud console or run the gcloud iam roles list --project=<your project name>, command to find the ID of the role that you wish to copy. By using the terminal command and the project name/value pair you will see only your custom roles created for that project which is a nice option.
Here is a screenshot of what it looks like in the google cloud console.
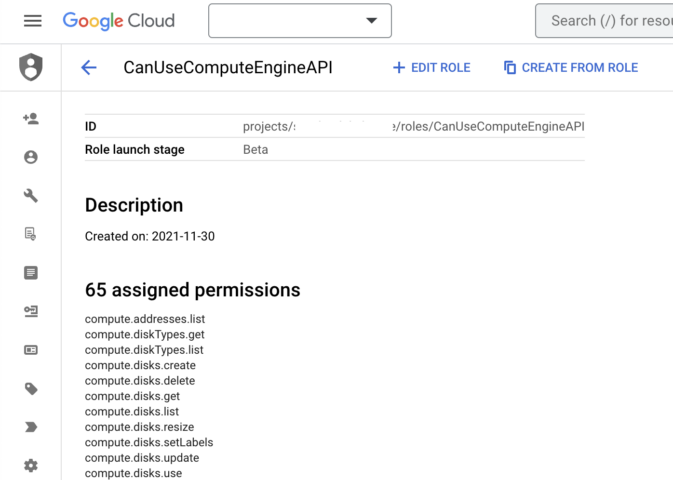
Capture the ID (using the UI) or the Name attribute value (if using the terminal) and save that for the next step.
NOTE: the ID that will be used in the command line is the part of the ID that starts with roles/. You will get an error if you run the command using the first part of the Id, projects/<project name>/, so for example roles/CanUseComputeEngineAPI, is the actual Id to use with the gcloud command.
Remember our goal is to copy the custom role with mainly existing (non-custom) gcp privileges that exist in any environment, from our development project, to the production project. So let’s do that now.
In the terminal window update the following command line to reflect your role Id, destination role name, and destination project Id
gcloud iam roles copy --source="<role Id>" --destination=<destination role name> --dest-project=<destination project Id>
So, for example your logic might look as follows:
gcloud iam roles copy --source-project=development-project --source="roles/CanUseComputeEngineAPI" --destination=CanUseComputeEngineAPI --dest-project=production-project
When running in the terminal you could face any one of these responses if you enter a portion of the above values incorrectly. But rest assured that this is possible, so check your syntax and confirm the names and values entered. If all else fails leave a comment or re-check the documentation:
- Invalid value for [source]: The role id should not include any ‘projects/’ or ‘organizations/’ prefix.
- Fix: you need to only use the name of the role
- Roles instance [CanUseComputeEngineAPI] not found: The role named roles/CanUseComputeEngineAPI was not found.
- Fix: you need to only use the name of the role
- Invalid value for [source]: The role id that starts with ‘roles/’ only stands for predefined role. Should not specify the project or organization for predefined roles
- Fix: you need to only use the name of the role
If you have any privileges that are declared by GCP to not be GA but rather in an alpha or beta stage, they will notify you upon a successful copy process, for example,
- Note: permissions [compute.instances.removeMaintenancePolicies, compute.instances.setDeletionProtection, compute.projects.setDefaultNetworkTier] are in ‘TESTING’ stage which means the functionality is not mature and they can go away in the future. This can break your workflows, so do not use them in production systems!
Summary
In this brief article, you learned how to copy a gcp role from one project to another. It is possible also to copy a role in the same project, basically a copy like, type of feature, but we have not covered that more simplistic scenario here. Hopefully, this helped to increase your knowledge of GCP IAM.